Google Workspace SAML integration
Google Workspace SAML integration
Google Workspace serving as an Identity Provider (IDP) can provide your users with single sign-on (SSO) access via Security Assertion Markup Language 2.0 Standard (SAML) to our Recorder and Video Editor under your team plan. When Team users first authenticate via SAML and you have configured SAML to create users, we set up their dedicated hosting account as part of the Team Plan.
This article describes how to configure SAML SSO with Google Workspace serving as the IDP.
Prerequisites
- Your organization must be using Google Workspace
- You will need administrative permissions for Google Workspace
- You must be using a ScreenPal Team Plan
- You will need administrative permissions for your Team Plan
Configuring SAML SSO with our app
1. Login into Google Workspace as an Administrator.
2. In your Google Apps Administration Console, click the Apps option.
3. In the Apps window, click SAML App.
4. Click the plus sign (+) option to add a new application.
5. Select Setup my Own Custom App.
6. Download the IDP Metadata file and save the file to your computer. Click Next.
7. Enter an application name and then click Next.
8. Keep the following tab open, as we will return to configure later:
9. Log into ScreenPal as a Team Admin, click your user icon, then select Settings.
10. On left sidebar, click Authentication.
11. Under SAML Authentication, move the toggle switch to On.
Once enabled, you will find the additional settings needed to set up communication between our app and the ADFS identity provider.
12. In the text box under Access URL, specify a unique access URL.
This URL will be used by your Team the first time they authenticate into our app. When visiting this URL, the user will be redirected to your organization network login for sign-in or, if they are already logged into your network, they will be automatically signed into our app.

Note: The "myuniqueurl" example shown below will be a name you create for your access page.
13. If you intend to have your users enjoy the advanced features provided in hosting (branded player, content sharing, channel carousel, stock images and videos, and so forth), select the checkbox for Create users on Screencast-O-Matic.
The first time a user from your organization logs in via SAML, their hosting account will be set up so they can manage and share content.
14. Next, download the metadata XML file underneath SAML Info in the settings area.
15. Click Choose File and upload the Google Apps IDP Metadata file you previously saved.
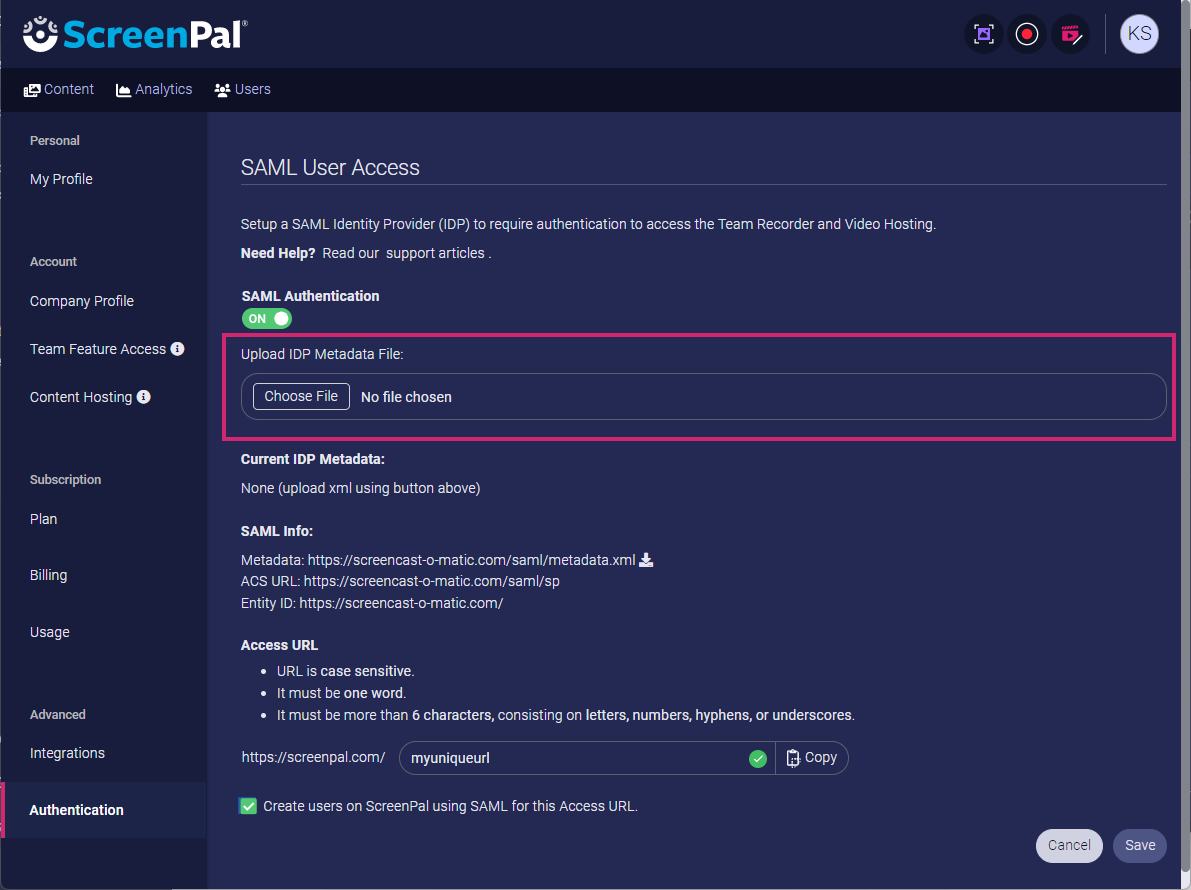
16. Copy the ACS URL and Entity ID for use in Google Apps.
17. Return to the Google Workspace tab or window, and paste the ACS URL and Entity ID into their respective fields.
Make sure to leave the defaults for Name ID set to Basic Information and Primary Email.
18. If you selected Create users on Screencast-O-Matic using SAML for this Access URL above, add Attributes to map First and Last Name for users. Otherwise, skip this step.
urn:oid:2.5.4.42 -> First Name (Basic Information)
urn:oid:2.5.4.4 -> Last Name (Basic Information)
19. Click Finish.
20. You should see the following screen with your installed app.
20. Return to the Screencast-O-Matic Authentication settings and click Save.
21. Click the Test Login link to make sure the login works.
You are all set! Now when your users land on the team access page they will be prompted to login via Google SSO.
Related Articles
Set up our app with ADFS SSO (SAML) for your organization
Set up our app with ADFS SSO (SAML) for your organization Active Directory Federation Services (ADFS) can provide your users with single sign-on (SSO) access via Security Assertion Markup Language 2.0 Standard (SAML) to your Team Plan. When Team ...Use ScreenPal with Google Docs, Google Sheets, and Google Slides
Google Docs, Google Slides and Google Sheets allow you to insert comments into your working project and for comments ScreenPal works great. Quick, personalized video comments can be very effective when collaborating on a project. If your colleague ...Add SAML Login using Premium Azure
Adding SAML Login using Premium Azure Once you have your ADFS server setup, your Team Plan admin may choose to optionally require login via SAML from the Admin Account Authentication Settings. 1. Log in as Team Admin and click your user icon, then ...Connect to a Google Drive account
Before you can import Google Slides for use in a Story project, you will need to connect your Google account to ScreenPal. To do this, complete the steps below. If you are looking for information about how to connect to Google Drive in order to save ...Share your recording on Google Classroom
Share your recording on Google Classroom You can use our app to create recordings and edit videos to easily share with students and teachers in Google Classroom. You can quickly share your videos from the desktop application or when accessing hosted ...